The Large Language Model (LLM) revolution is well underway, and even early adopters are still relying on conventional cyber security tools.
This oversight is understandable; even inevitable. LLMs have introduced rapid change, leaving many organizations in a race to catch up. Nevertheless, relying on traditional cyber security tools to secure LLMs is like bringing a knife to a gunfight. In addition to the threats we know about, new ones are evolving all the time. Meeting this challenge requires specific expertise and focus in LLMs.
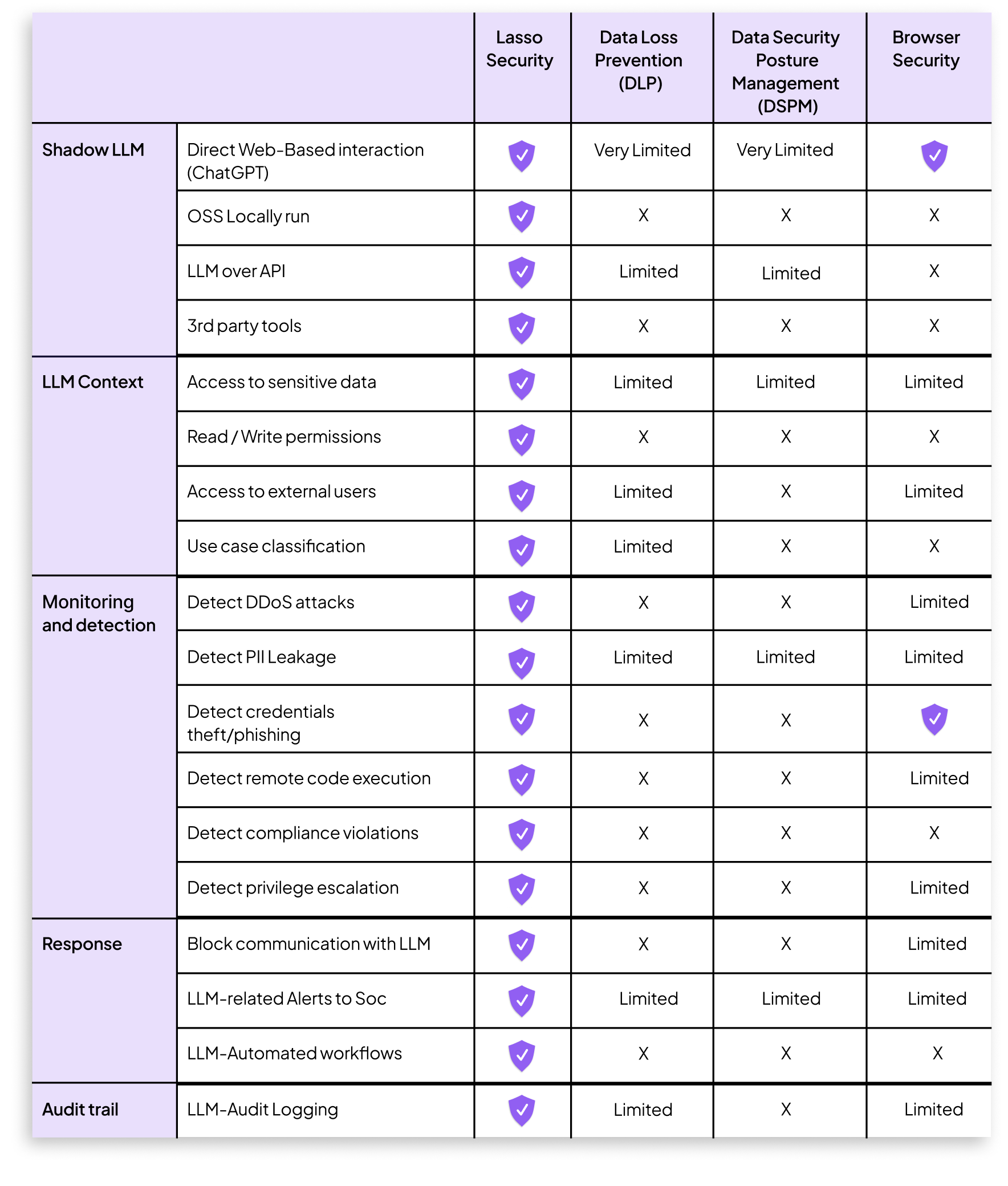
In this article, we’re exploring some of the most common frameworks and their limitations when it comes to safeguarding LLMs - and by extension, the users who are increasingly interacting with them daily. This groundbreaking technology requires a dedicated solution, not a mere feature; rather a full LLM security suite comprehensive solution, focused on the LLM world.
LLMs are increasingly functioning like an operating system, with features such as:
In the future, they will act as agents with specific access and permissions. This makes LLM security a complex and urgent priority. As these models gain more autonomy and deeper integration into various systems, they become potential targets for sophisticated cyber threats. As LLMs evolve, so too must our approach to safeguarding them and the data they process.
Cyber security now encompasses over 40 distinct subdomains. This alone makes it impossible for any single vendor to address the whole breadth of the cybersecurity landscape. Even worse, the rapid pace of LLM development will continue to shift the goalposts for larger, less agile vendors.
Traditional cybersecurity vendors may excel in areas like code scanning, malware detection, and infrastructure configurations, but these capabilities don't align with the unique challenges of securing LLMs.
In addition, LLMs can handle a diverse range of tasks, including complex ones. Thus, LLM attacks are very broad, and not specifically focused like what existing tools aim to prevent.
The first of these is identifying which LLMs are actually in use within an organization, and how - the so-called “Shadow AI” problem. They can be accessed via web browsing directly (e.g. ChatGPT), via 3rd party vendors’ applications, as part of an organization’s own application or internal tool, or through several other means such as API calls.
Detecting and identifying all of these is not a capability that most security vendors have. Now that there are hundreds (maybe thousands) of these entry points, a vendor with a generic approach cannot secure them all. This calls for an LLM-focused solution.
Understanding the risk potential, context, access to data and actions, and goal of each LLM is a crucial part of protecting the organization, setting a baseline for usage and effectively monitoring the use of the LLM, limiting the number of false positives and keeping the organization running without background noises.
Existing tools lack the capacity to understand the context of each LLM interaction. Without context, there’s no way to identify anomalies and threats, let alone respond to them by escalating to security operations teams. Most existing security tools expect structural interactions, but LLMs are inherently more contextual and conversation-based, making these tools largely obsolete.
Let’s consider a range of common cyber security tools, which LLM protection is not in their core, and their specific shortcomings when it comes to securing LLMs.
LLMs have transformed the way users interact with text-based information, from chatbots to content generation. While robust browser security measures are vital for general online safety, securing LLMs requires a unique approach.
Here's why relying solely on browser security isn't enough once LLMs enter the picture:
Browser security tools lack the depth and specificity to monitor user interactions with LLMs. Effective monitoring should extend beyond browser-level security to capture the behavior and content generated by LLMs. More than that, some browser security tools try to offer a solution for ChatGPT only, while there are already hundreds of tools out there which are in use (e.g. Bard, Claude).
Browser security mechanisms deal with detecting and attacking web-borne threats and risks that attempt to attack the browser itself or exploit it as an attack vector.
While those deal with static rendering of web pages, LLMs operate in a real-time, text-based conversational context. That context includes diverse natural language queries, commands, and contextual information.
This introduces a high degree of unpredictability. Users can pose a wide array of queries, from factual inquiries to creative requests. All of this makes it difficult for conventional browser security to comprehend the context, intent, and appropriateness of the content that LLMs generate. For example, browser security tools can prevent PII leakage in basic cases. But more advanced cases like prompt injection are beyond their capabilities. In addition, when an execution takes place inside the LLM (for example, the ChatGPT plugin), browsers can't see it.
Protecting users and employees is only one part of the picture. Once LLM interactions take place in the backend, browser security becomes irrelevant and leaves a gap to bypass the security laye.
Next, let’s consider the limitations of Data Loss Prevention (DLP) and Data Security Posture Management (DSPM). These systems, though effective in their domains, face unique challenges when confronted with the dynamic and complex nature of Large Language Models (LLMs).
Data Loss Prevention (DLP) is a comprehensive cyber security framework for safeguarding sensitive information within an organization. It involves policies, tools, and technologies to detect, monitor, and prevent unauthorized access, sharing, or leakage of confidential data. DLP is primarily used to protect sensitive data such as customer information, intellectual property, financial records, and personal identifiable information (PII).
Data Loss Prevention (DLP) systems function by identifying, monitoring, and protecting data in use, in motion, and at rest through deep content inspection and contextual analysis of transactions. This includes patterns like the regex for credit card numbers. A DLP solution will immediately flag any code that matches this pattern, potentially preventing many instances of credit card fraud.
But an intelligent attacker can get a bit more sophisticated and cue an LLM to incrementally reveal that data, exploiting the contextual nature of the LLM, using a method like Jailbreak and prompt injection. This approach leverages the LLM's ability to engage in contextually rich conversations and manipulate a user's perceptions. In situations like these, a DLP system loses its relevance and cannot prevent that kind of a data breach.
Essentially, DLP focuses primarily on what leaves the organization, but can’t tell what is getting into the organization - in this case, through the response of the LLM. Many organizations do not want to be exposed to sensitive data getting into the organization, for example, copyrights which may cause legal issues, or rogue pieces of code that can get into the developer's workspaces.
Different LLMs behave differently, whether it is because they are aimed towards different tasks, or because they are trained on different data sets and create different models.
Therefore, a security tool has to have an intimate understanding of the different LLMs out there, and usually, DLP solutions tend to be very generic, requiring a lot of customizations and rules, which eventually also create a lot of false positive alerts.
Data Security Posture Management is an emerging body of technologies and techniques for protecting sensitive data in cloud stores. It typically involves identifying where sensitive data is stored in managed warehouses or unmanaged databases, and then classifying this data according to various levels of static risk analysis, making sure that sensitive records are not exposed and used in an unauthorized manner.
For DSPMs, an LLM is just yet another data store. This is an inaccurate way to treat LLMs, and it results in major blindspots.
Like the other tools we have aready discussed, DSPM tools cannot analyze the semantic nuances, context, and conversation nature of the language used in interactions with LLMs. In the same way, as described above, a sophisticated attacker can apply prompt injection techniques to extract sensitive data out of the LLM, while overriding the configured policies. More than that, the DSPMs, like a lot of other tools, are looking into the organization making sure its data is not exposed, while not looking at all into the data that might get into the organization.
While DSPMs focus on cloud environments, a lot of LLMs are already available in the form of open-source models, which an organization can deploy on-prem and run locally.
More than that, a lot of the interactions with LLMs are web-based. And there, DPSM tools have only marginal utility, which does not address the challenges of using tools like ChatGPT.
In a rapidly evolving digital landscape, securing LLMs demands specialized solutions that transcend traditional cybersecurity tools. At Lasso, we recognize the unique security challenges posed by LLMs. To address these challenges, we have developed a cutting-edge cybersecurity solution specifically designed to safeguard these transformative models.
Get in touch to find out how our LLM-focused cybersecurity solution empowers organizations to navigate LLM security challenges with confidence.